Recently I've been studying various cybersecurity topics in an effort to make a career change. To that end, I've been making an effort to get hands-on and simulate as much real-world experience as I can. In the interest of learning about SOC functions, I decided to set up a SIEM system on my home network. This page will document the process I followed to install and configure Wazuh at home. First, I'll address some of the reasoning behind this decision.
A SIEM (Security Information and Event Management) system is a comprehensive solution that helps organizations collect, analyze, and respond to security events in real-time. It acts as a central hub for monitoring and managing security alerts, making it easier to detect and mitigate threats. It's the bread and butter of entry-level SOC jobs, and likely the tool I'll end up using the most when I find one.
While SIEM systems are typically associated with large enterprises, setting up a SIEM at home is a valuable learning experience. By monitoring my home network, I aim to gain a better understanding of tools and processes used to detect threats and vulnerabilities in the real world.
Wazuh is an open source SIEM using an ELK backend. While the specifics of a particular task will vary between SIEM solutions, the fundamental design is very similar to more expensive software. Having experience with deploying ELK as a SIEM already it was a natural fit for my $0 budget and past experience. My areas of focus for this exercise were logging, event monitoring, vulnerability scanning, and compliance monitoring. All are features Wazuh supports out of the box, with all but vulnerability scans turned on by default.
I've recently torn down my old stack of rack mount hardware, so for now I'll be virtualizing things on one of my work stations instead of running VMs on Proxmox as I typically would. I'll be using Virtualbox on Windows, but this can just as easily be accomplished with virt-manager, docker, or any other virtualization tech.
To give a brief overview of the setup process: (Wazuh provides excellent documentation here)
I created a new VM in VirtualBox and specified the RAM, CPU, and storage resources. I configured the VM's networking as a bridged connection, since the Wazuh install needs to be accessible to the rest of the endpoints on the network, and NAT typically uses a separate subnet. After launching the VM, I initiated the Ubuntu installation process and updated and upgraded packages post-installation.
Once Ubuntu was up to date the process went fairly smoothly. Installing the Wazuh was a simple plug and chug following the directions from the documentation. Once the management page was available on the network I installed the Wazuh agent on some Windows workstations, an Ubuntu 22 workstation, and two Raspberry Pis. Logs started showing up immediately, and after some time vulnerability scans began to show up as well.
It's worth noting that the only trouble I had during setup was with the Vulnerability scanning. There isn't any way to trigger a scan manually, and I wasn't able to find a work around for the issue. I ended up just enabling and configuring the vulnerability scans and waiting 24 hours for the first results to come in. Thankfully they did and have been coming in regularly since. From what I was able to find in my research into it I think this is somewhat expected behavior, but clearly an oversight from a UX perspective. Who wouldn't want to run a scan right away to confirm the agent is working correctly? I would be surprised if it's not a feature we see added in a future update.
After setting up Wazuh I was finally able to do some vulnerability scans on some of my systems. Having had previous experience with developing in secure environments I wasn't surprised to see that my unmanaged endpoints had vulnerabilities. What was initially mildly surprising was how many more vulnerabilites my Ubuntu workstation had compared to my Windows workstation.
Windows
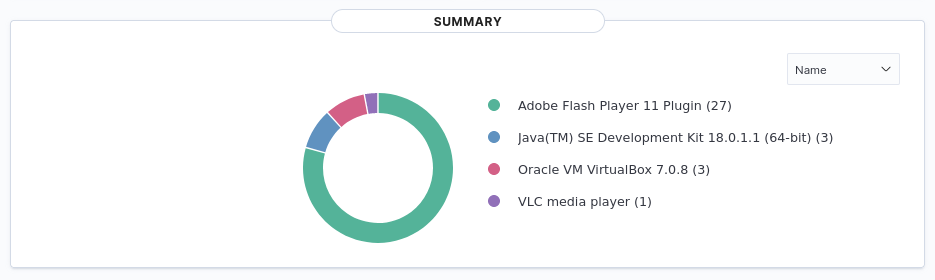
Ubuntu 22
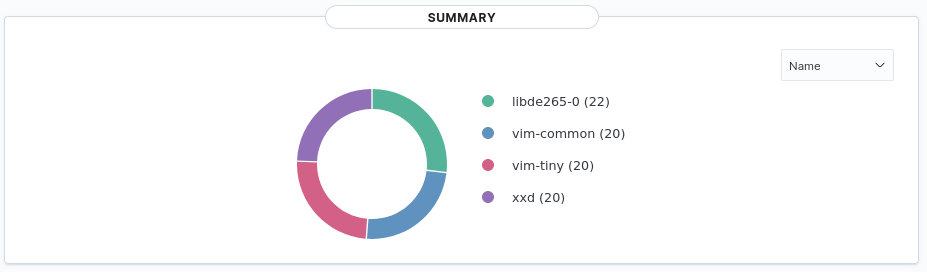
In hindsight I suppose it's not actually that surprising. In a past position the security team I would develop with hated dealing with Ubuntu because it introduced so many CVEs they had to mitigate. I suspect if I were using RHEL or CentOS the results would be closer.
Remediating the windows CVEs will require updating some software that's out of date. Ubuntu will prove more difficult since the vulnerabilities haven't been addressed by Canonical and are pre-installed packages that come with Ubuntu. Updating these beyond the latest included version may cause unexpected issues, and may not be worth the hassle on a system that isn't public-facing. Some further risk analysis will have to take place before remediation in these cases.
Setting up Wazuh on my home network gave me some hands-on experience with a SIEM. In the future I'll use Wazuh to create custom rules and track the success of my vulnerability remediation efforts. In future labs I will install an IDS/IPS along side wazuh, do some data recovery on damaged hard drives, and simulate some attacks on my own network to test my ability to penetrate systems and detect suspicious activity.